Principles of Cyber Security
March 2024
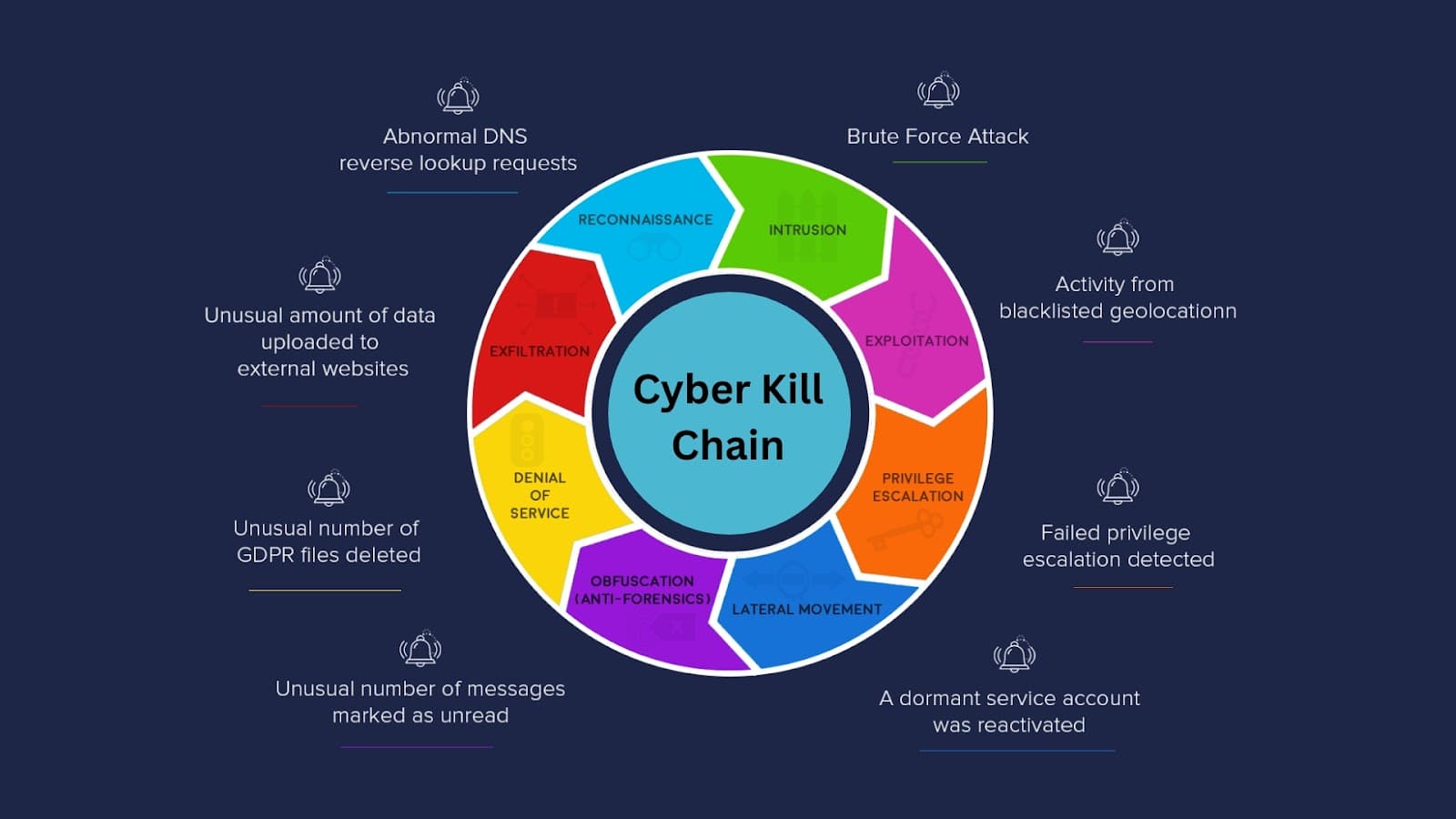
Applied the kill chain model to analyse cyber-attacks and evaluate threat actor profiles.
Hi! My name is
Designing, building, and monitoring security functions
Cybersecurity graduate with a First-Class BSc in Computer Science (University of Southampton, 2025) and hands-on experience across enterprise security, cloud security, and penetration testing. CompTIA Security+ certified and ranked in the top 1% on TryHackMe, with proven skills in SecOps, DevSecOps, and offensive security through CTFs and exploitation labs. Experienced in securing cloud infrastructure with Terraform, developing APIs with Python/FastAPI, and integrating security into CI/CD pipelines. Proficient in penetration testing tools including Burp Suite, Nmap, Wireshark, Metasploit, and Kali Linux. Proven communicator with experience delivering security workshops to technology departments and translating complex concepts for diverse audiences.


March 2024
Applied the kill chain model to analyse cyber-attacks and evaluate threat actor profiles.

November 2024 - January 2025
Explored cloud and web application security, emphasising attack and defence strategies to enhance cybersecurity knowledge.
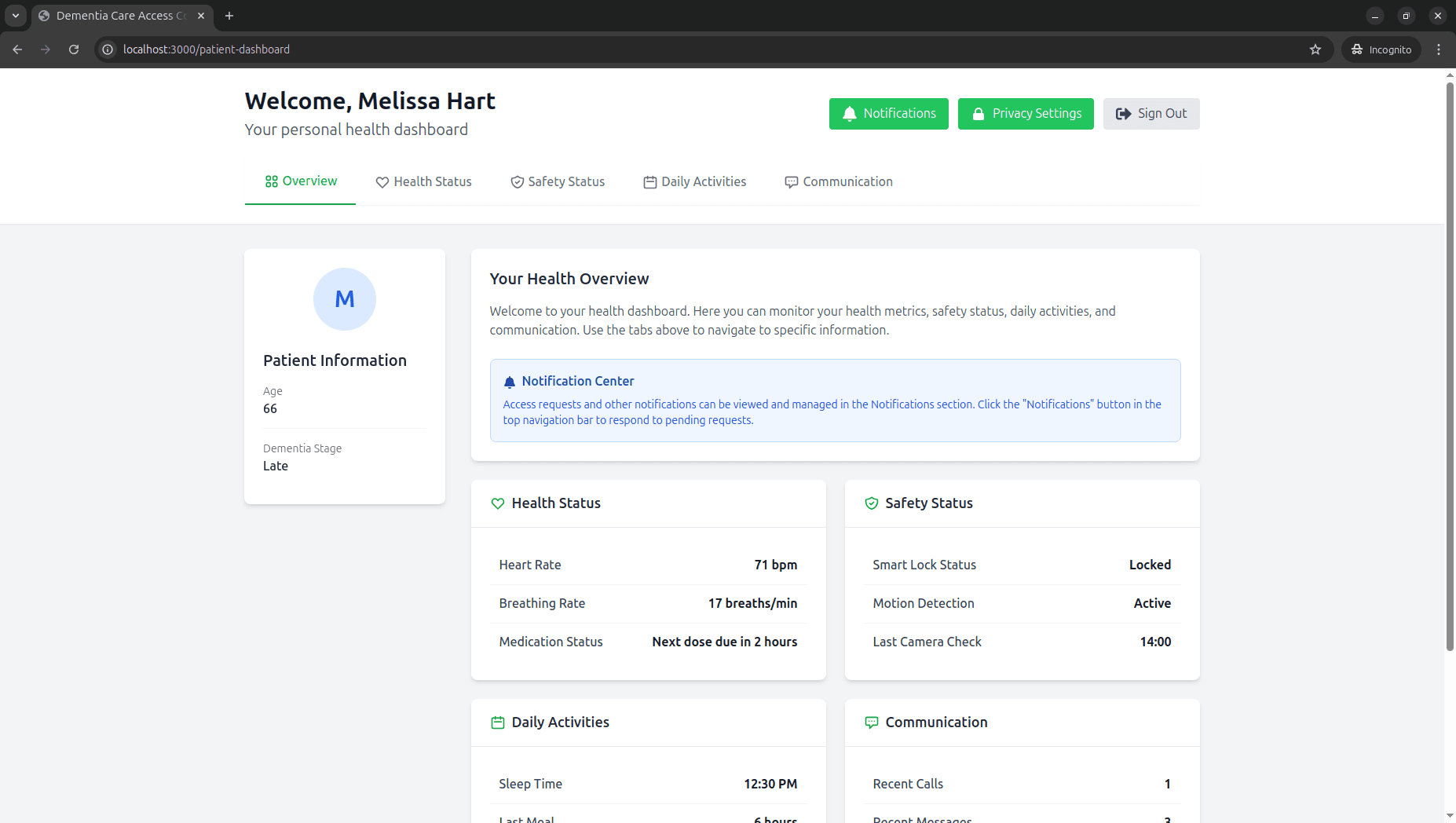
September 2024 - October 2025
Built a proof-of-concept access control system connecting multiple IoT data sources for people with dementia, based on security principles. The system is designed for cloud deployment and cross-device compatibility.